
King Phisher
- 0 ratings

King Phisher is a tool for testing and promoting user awareness by simulating real world phishing attacks.
Self-host this app for $0.99/mo only!




Phishing Campaign Toolkit
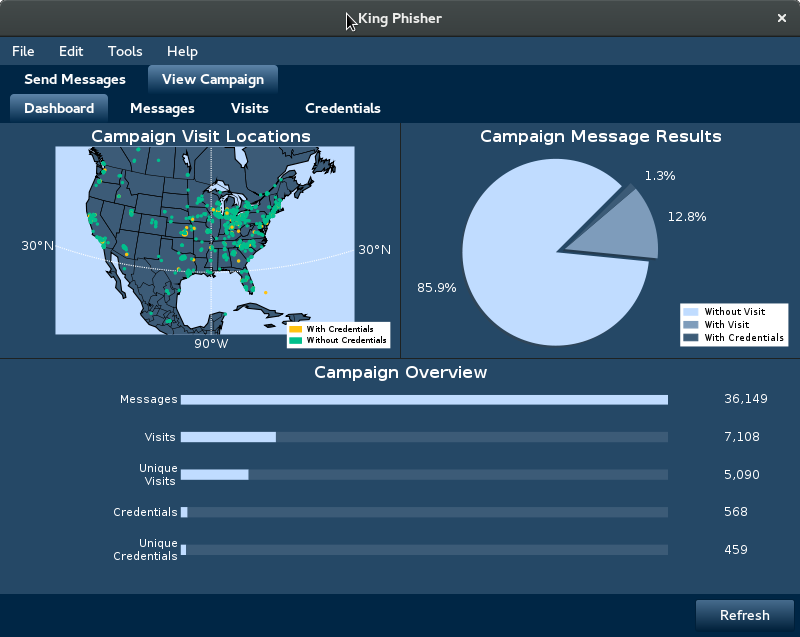
For instructions on how to install, please see the INSTALL.md file. After installing, for instructions on how to get started please see the wiki.
King Phisher is a tool for testing and promoting user awareness by simulating real world phishing attacks. It features an easy to use, yet very flexible architecture allowing full control over both emails and server content. King Phisher can be used to run campaigns ranging from simple awareness training to more complicated scenarios in which user aware content is served for harvesting credentials.
King Phisher is only to be used for legal applications when the explicit permission of the targeted organization has been obtained.
Get the latest stable version from the GitHub Releases Page or use git to checkout the project from source.
Both the client and server can be extended with functionality provided by plugins. A small number of plugins are packaged with King Phisher and additional ones are available in the Plugins repository.
Template files for both messages and server pages can be found in the separate King Phisher Templates repository. Any contributions regarding templates should also be submitted via a pull request to the templates repository.
Documentation for users of the application is provided on the project's wiki page. This includes steps to help new users get started with their first campaigns. Additional technical documentation intended for developers is kept separate as outlined in section below.
King Phisher uses Sphinx for internal technical documentation. This
documentation can be generated from source with the command
sphinx-build -b html docs/source docs/html. The latest documentation is
kindly hosted on ReadTheDocs at
king-phisher.readthedocs.io.
The client message templates are formatted using the Jinja2 templating engine and support a number of variables. These are included here as a reference, check the templates wiki page for comprehensive documentation.
| Variable Name | Variable Value |
|---|---|
| client.company_name | The target's company name |
| client.email_address | The target's email address |
| client.first_name | The target's first name |
| client.last_name | The target's last name |
| client.message_id | The unique tracking identifier (this is the same as uid) |
| sender.email | The email address in the "Source Email (MIME)" field |
| sender.friendly_alias | The value of the "Friendly Alias" field |
| sender.reply_to | The value of the "Reply To" field |
| url.tracking_dot | URL of an image used for message tracking |
| url.webserver | Phishing server URL with the uid parameter |
| url.webserver_raw | Phishing server URL without any parameters |
| tracking_dot_image_tag | The tracking image in a preformatted <img /> tag |
| uid | The unique tracking identifier (this is the same as client.message_id) |
The uid is the most important, and must be present in links that the messages contain.
King Phisher is released under the BSD 3-clause license, for more details see the LICENSE file.
Special Thanks (QA / Beta Testing):
King Phisher Development Team:
Please login to review this project.
No reviews for this project yet.
Instant terminal sharing.
Infrastracture behind a web UI for GNU Octave, the libre al…
A self hosted virtual browser (rabb.it clone) that runs in …
Comments (0)
Please login to join the discussion on this project.